Autonomous Networks Beyond 5G
It has become evident that migration to 5G based on templates for services and network slices hard-coded into operators’ systems does not scale for B5G scenarios, where the network should adapt to the end users’ needs in a dynamic and on-demand manner. Network automation is the only way to deal with such adaptive environments. SDN promised the capability to program the network, and there are tools to do it. However, each tool has its own APIs, their associated data models may vary and may be proprietary, so integration is a costly and time-consuming process.
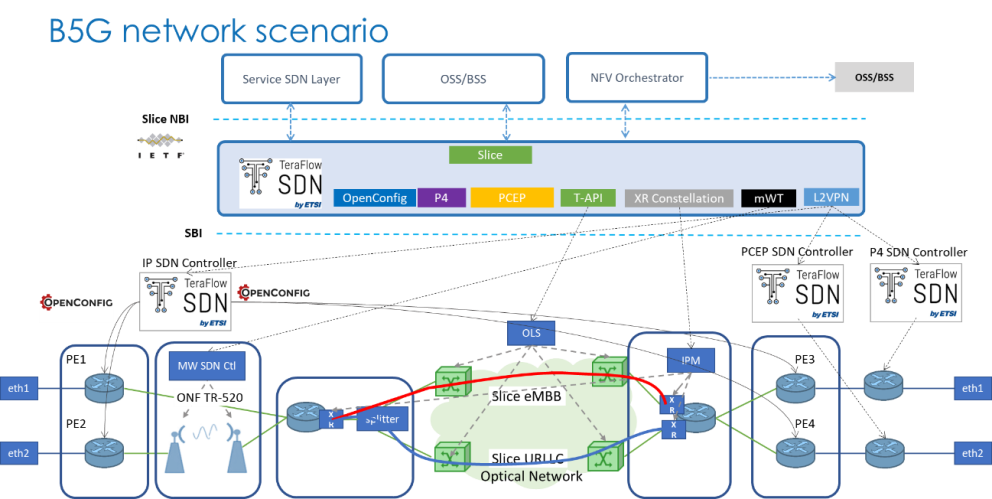
TeraFlowSDN controller supports a set of operator-driven use cases and workflows that include the objectives of this scenario dealing with the programmability of network elements and technology-based SDN controllers with the north bound and south bound interface requirements.
The figure below provides the high-level architecture of this scenario. A set of multiple integrated network elements are considered in network technological domains and used to support the autonomous provisioning and subsequent configuration and management of transport network slices, consisting of multiple Virtual Private Network (VPN) services such as Layer 2 (L2VPN) and Layer 3 (L3VPN) services with dedicated Service Level Agreements (SLA). Another possibility is the interaction of an NFV Orchestrator (e.g., ETSI OpenSource MANO) with TeraFlowSDN North-Bound Interfaces (NBI), which includes provisioning L2/L3VPN connectivity. This scenario shows how the TeraFlowSDN controller can trigger the necessary handlers to interact with the underlying technological domains in all these service requests.
Inter-domain
The second scenario focuses on the inter-domain deployment of transport network slices, looking at the deployment challenges of Cooperative, Connected and Automated Mobility (CCAM) services over a distributed edge and cloud infrastructure: unified computing, storage, and networking resources management, multi-domain networking and multi-domain belonging to different network operators.
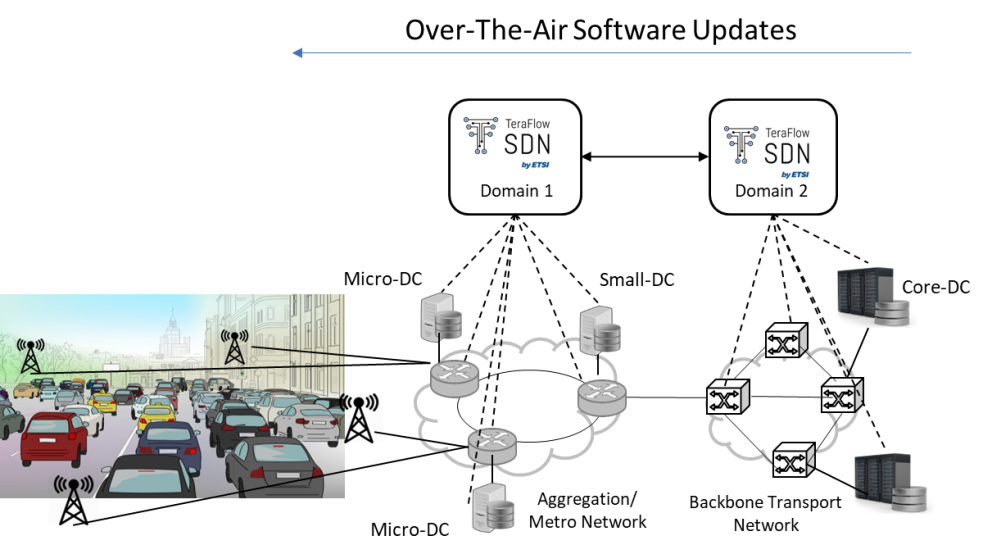
At the infrastructure layer, the scenario comprises several packet and optical transport networks for the metro and the core segments, providing connectivity to the distributed cloud and edge computing infrastructure. CCAM services can be deployed in micro-DCs at the edge nodes (e.g., cell sites, street cabinets, lampposts), small-DCs (e.g., in a central office) for low/moderate-computation capacity and low response time, and core-DCs in the core network for high-computational capacity and moderate response time.
In this scenario, transport and cloud infrastructures are administratively partitioned into different domains, each controlled by a TeraFlowSDN Controller instance. In addition to selected uplink-heavy and latency-sensitive scenarios, the intention is to focus on Over-the-Air (OTA) software updates, which are software improvements that a car company sends wirelessly to vehicles. These OTA updates need to reach a moving target; thus, we provide an inter-domain scenario for moving connectivity services based on the position of the network elements. Testing and experimentation will be necessary to address the role of the Transport Network Slice and its endpoints regarding the interaction with adjacent access and service edge (SDN) control domains in this inter-domain scenario.
Cybersecurity
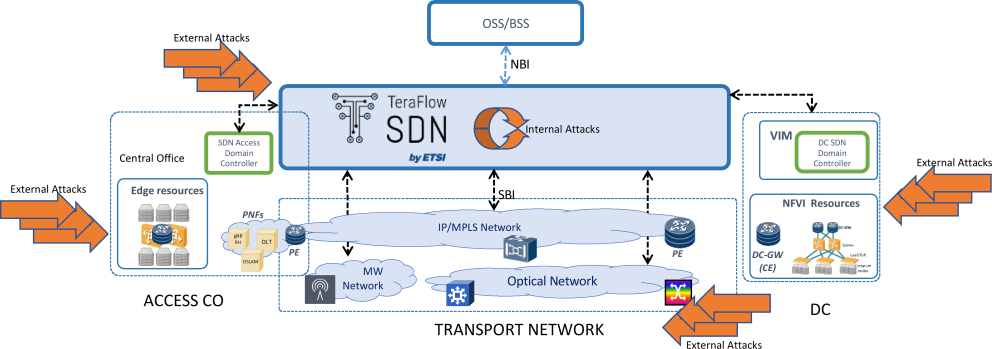
Nowadays, when an operator moves towards an automated environment, security becomes a key feature since network operations are done by software components operating without human intervention or oversight. Moreover, the pervasive softwarisation of network and infrastructure components is further increasing their attack surface. Indeed, security must undergo a similar technological evolution to enable the resilience of SDN controllers: automation of security policies over the network, use of Machine Learning (ML) to detect and identify attacks, utilization of DLT to ensure configuration and forensic capacity, and deployment of NFV security functions.
This scenario demonstrates a combination of innovative solutions that are scalable in a production environment and resilient to sophisticated attacks in a common framework that integrates different security technologies to detect, identify, and mitigate both traditional and new generations of attacks across different technology domains, e.g., optical and IP layers. At the control plane, the SDN controller and the ML models that support its operations may also be the target of malicious attacks.
For the Layer 3 cybersecurity experiments, the scenario proposes a setup that allows us to reproduce previously recorded cryptomining attacks. We first capture packets from the cryptomining attack that are reproduced in the setup environment. Second, the objective of the optical physical layer attacks is to reproduce previously-capture Optical Performance Monitoring (OPM) data from malicious attack conditions.